Docker Cheat Sheet for use with docker cli.
System
Version
Info
Stats
Docker run is a combination of (optionally) docker pull, docker create, and docker start. See also Docker run reference. Create a container from my-image, and run the default command: docker run my-image; Run the echo command in the container instead of the default command: docker run my-image echo 'hello' Run container in the background: docker run -d my-image; Run and remove the container after it exits: docker run -rm my-image. Docker Cheat Sheet. Pull the Docker repository; docker pull wpscanteam/wpscan. Run WPScan and enumerate usernames; docker run -it -rm wpscanteam/wpscan -url -enumerate u. When using -output flag along with the WPScan Docker image, a bind mount must be used. Otherwise, the file is written inside the Docker container, which is then thrown away.
System Components
Prune all unused and dangling images
Login
Logout
Network
List
Create
Inspect
Connect Container
Disconnect Container
Remove
Images
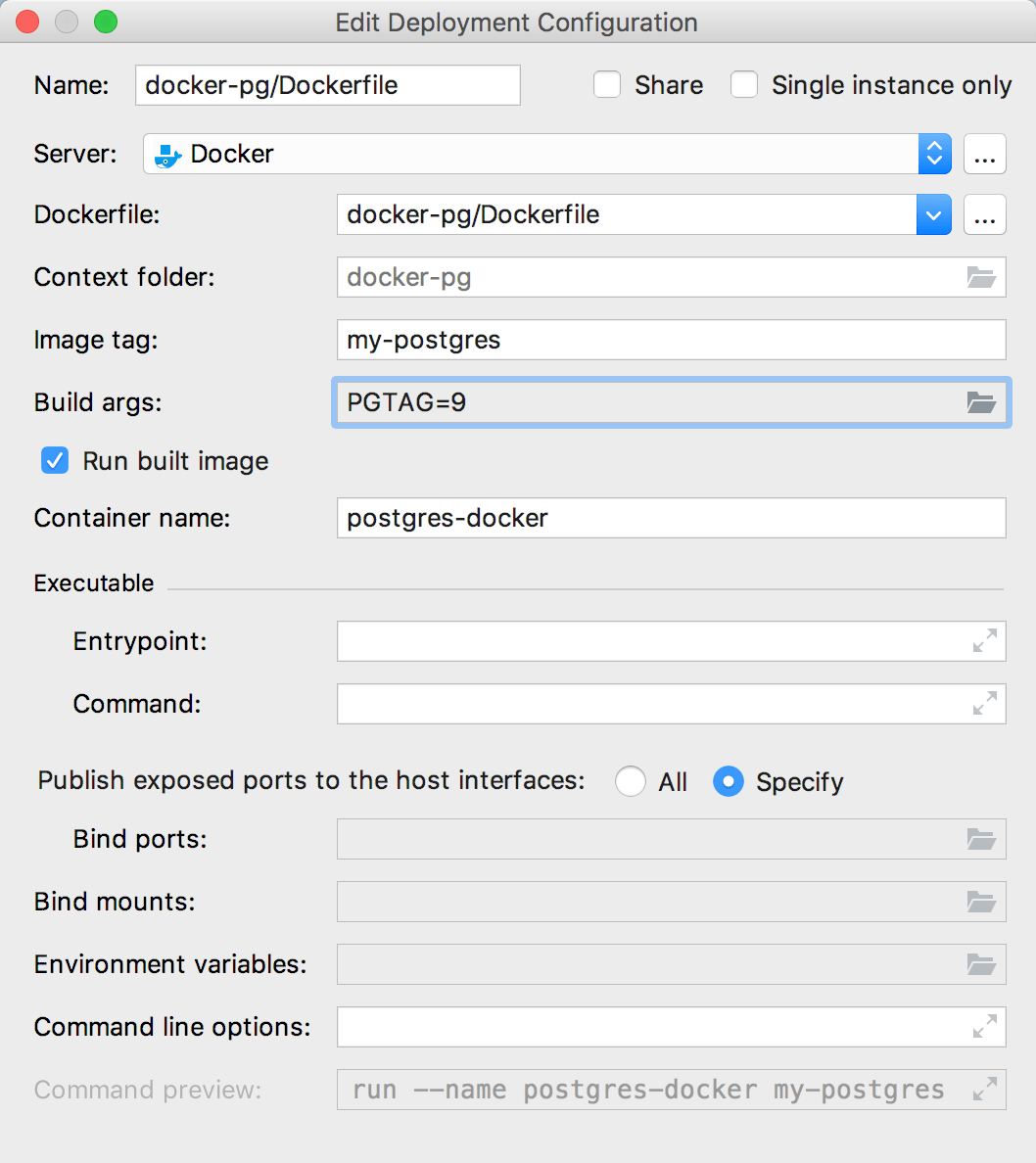
Build (from Dockerfile in root context)
Build (from Dockerfile in another folder)
List used
Docker Build Cheat Sheet
List all
Remove
Remove unused
Remove dangling
Remove all
Containers
List running
List all
Inspect
Create
Run
Run flags
| -rm | Automatically remove container once stopped |
| -it | Allocates command line to container’s STDIN |
| -d | Run container in detached mode, ie. background |
| -v | Mount a volume Example with new volume: -v /local-folder:/container-folder Example with existing volume: -v [VOLUME NAME]:/container-folder |
| -p | Binds port from container to local env Example: -p local-port:container-port |
Enter bash
Enter shell
Enter powershell
Start
Stop one
Stop all
Remove
Remove all
Remove all (force running ones)
Remove all (force running ones plus volume)
Logs
Volumes
List
Create
Inspect
Remove
Remove unused
Remove dangling
Remove active
Compose
Up from File
Down from File
File Operations
Docker Cheat Sheet Pdf
Copy to container or volume
Docker Engine
Switch to Linux Mode
Switch to Windows Mode
Last week, we announced that the Docker Desktop Stable release includes vulnerability scanning, the latest milestone in our container security solution that we are building with our partner Snyk. You can now run Snyk vulnerability scans directly from the Docker Desktop CLI. Combining this functionality with Docker Hub scanning functionality that we launched in October provides you with the flexibility of including vulnerability scanning along multiple points of your development inner loop, and provides better tooling for deploying secure applications.
You can decide if you want to run your first scans from the Desktop CLI side, or from the Hub. Customers that have used Docker for a while tend to prefer starting from the Hub. The easiest way to jump in is to configure the Docker Hub repos to automatically trigger scanning every time that you push an image into that repo. This option is configurable for each repository, so that you can decide how to onboard these scans into your security program. (Docker Hub image is available only for Docker Pro and Team subscribers, for more information about subscriptions visit the Docker Pricing Page.)
Once you enable scanning, you can view the scanning results either in the Docker Hub, or directly from the Docker Desktop app as described in this blog.
From the scan results summary you can drill down to first view the more detailed data for each scan and get more detailed information about each vulnerability type. The most useful information in vulnerability data is the Snyk recommendation on how to remediate the detected vulnerability, and if a higher package version is available where the specific vulnerability has already been addressed.
Detect, Then Remediate
If you are viewing vulnerability data from the Docker Desktop, you can start remediating vulnerabilities, and testing remediations directly from your CLI. Triggering scans from Docker Desktop is simple – just run docker scan, and you can run iterative tests that confirm successful remediation before pushing the image back into the Hub.
For new Docker users, consider running your first scans from the Desktop CLI. Docker Desktop Vulnerability Scanning CLI Cheat Sheet is a fantastic resource for getting started.
The CLI Cheat Sheet starts from the basics, which are also described in the Docker Documentation page on Vulnerability scanning for Docker local images – including steps for running your first scans, description of the vulnerability information included with each scan result, and docker scan flags that help you specify the scan results that you want to view. Some of these docker scan flags are –
Docker Command Cheat Sheet
--dependency-tree -displaying the list of all the package underlying dependencies that include the reported vulnerability--exclude base -running an image scan, without reporting vulnerabilities associated with the base layer--f -including the vulnerability data for the associated Dockerfile--json -displaying the vulnerability data in JSON format
The really cool thing about this Cheat Sheet is that it shows you how to combine these flags to create a number of options for viewing your data – Archicad 18 for mac os x.
- Show only high severity vulnerabilities from layers other than the base image:
$ docker scan myapp:mytag --exclude-base --file path/to/Dockerfile --json | jq '[.vulnerabilities[] | select(.severity'high')]'
- Show high severity vulnerabilities with an CVSSv3 network attack vector:
$ docker scan myapp:mytag --json | jq '[.vulnerabilities[] | select(.severity'high') | select(.CVSSv3 | contains('AV:N'))]'
- Show high severity vulnerabilities with a fix available:
$ docker scan myapp:mytag --json | jq '[.vulnerabilities[] | select(.nearestFixedInVersion) | select(.severity'high')]'
Running the CLI scans and remediating vulnerabilities before you push your images to the Hub, reduces the number of vulnerabilities reported in the Hub scan, providing your team with a faster and more streamlined build cycle
Docker Cheat Sheet 2020
To learn more about running vulnerability scanning on Docker images, you can watch “Securing Containers Directly from Docker Desktop” session, presented during SnykCon. This is a joint presentation by Justin Cormack, Docker security lead, and Danielle Inbar, Snyk product manager, discussing what you can do to leverage this new solution in the security programs of your organization
