 I ran into an issue recently regarding an unstable AnyConnect VPN connection from a laptop, through a DSL router (not mine), terminating at a Cisco ASA running IOS 9.1. The laptop, running Windows 8 (yes, I know), had AnyConnect 3.1 installed on it. The problem was the AnyConnect connection would connect every time, but after about 1 or 2 minutes, it would disconnect.
I ran into an issue recently regarding an unstable AnyConnect VPN connection from a laptop, through a DSL router (not mine), terminating at a Cisco ASA running IOS 9.1. The laptop, running Windows 8 (yes, I know), had AnyConnect 3.1 installed on it. The problem was the AnyConnect connection would connect every time, but after about 1 or 2 minutes, it would disconnect.Anyconnect ask enable default webvpn immediately goes to the portal page. Anyconnect ask enable default timeout value prompts the remote user to download the client or go to the clientless portal page and waits the duration of value before taking the default action—downloading the client. We would like to show you a description here but the site won’t allow us. If you have more than one client package you can specify the relevant order by entering the following configuration and enable AnyConnect. ASA(config-webvpn)# anyconnect image flash:/anyconnect-win-4.6.02074-webdeploy-k9.pkg 1 ASA(config-webvpn)# anyconnect enable Create a VPN IP Pool. Install java runtime for mac. Create an IP pool that will be used for RA VPN users. Anyconnect can use DTLS. You can configure DTLS port and enable it on the ASA as following. When you enable WebVPN on an interface, both TLS and DTLS are enabled on the interface, if you don't specify 'tls-only' option. Actionscript for mac. Asa2(config-webvpn)# enable outisde. Rise of nations for mac os.
The logs in the ASA indicated that the user session was being terminated on the remote end:
%ASA-5-722037: Group
ASA/pri/act#show vpn-sessiondb anyconnect
Session Type: AnyConnect
Username : USERA Index : 229
Assigned IP : x.x.x.x Public IP : x.x.x.x
Protocol : AnyConnect-Parent SSL-Tunnel DTLS-Tunnel
License : AnyConnect Essentials
Encryption : AnyConnect-Parent: (1)none SSL-Tunnel: (1)DES DTLS-Tunnel: (1)DES
Anyconnect Webvpn Configuration
Hashing : AnyConnect-Parent: (1)none SSL-Tunnel: (1)SHA1 DTLS-Tunnel: (1)SHA1
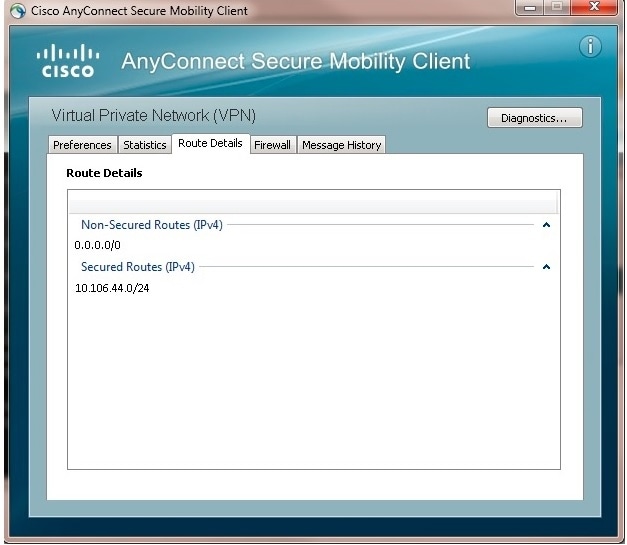
Bytes Tx : 699061 Bytes Rx : 245379
Group Policy : GroupPolicy_VPN Tunnel Group : VPN
Login Time : 10:37:45 EST Tue Feb 26 2013

Duration : 0h:41m:04s
Inactivity : 0h:00m:00s
NAC Result : Unknown
VLAN Mapping : N/A VLAN : none
Username : USERB Index : 236
Assigned IP : x.x.x.x Public IP : x.x.x.x
Protocol : AnyConnect-Parent SSL-Tunnel
License : AnyConnect Essentials
Anyconnect Webvpn Web
Encryption : AnyConnect-Parent: (1)none SSL-Tunnel: (1)DES
Hashing : AnyConnect-Parent: (1)none SSL-Tunnel: (1)SHA1
Bytes Tx : 59422 Bytes Rx : 36304
Group Policy : GroupPolicy_VPN Tunnel Group : VPN
 Login Time : 11:15:31 EST Tue Feb 26 2013
Login Time : 11:15:31 EST Tue Feb 26 2013Duration : 0h:01m:18s
Inactivity : 0h:00m:00s
NAC Result : Unknown
VLAN Mapping : N/A VLAN : none
The following text I found somewhere on Cisco's support forum site, linked here, which helped me figure out the issue.
The SSL-Tunnel is the TCP tunnel that is first created to the ASA. When it is fully established, the client will then try to negotiate a UDP DTLS-Tunnel. While the DTLS-Tunnel is being established, data can pass over the SSL-Tunnel. When the DTLS-Tunnel is fully established, all data now moves to the DTLS-tunnel and the SSL-tunnel is only used for occasional control channel traffic. If something should happen to UDP, the DTLS-Tunnel will be torn down and all data will pass through the SSL-Tunnel again.
The decision of how to send the data is very dynamic. As each network bound data packet is processed there is a point in the code where the decision is made to use either the SSL connection or the DTLS connection. If the DTLS connection is healthy at that moment, the packet is sent via the DTLS connection. Otherwise it is sent via the SSL connection.
The SSL connection is established first and data is passed over this connection while attempting to establish a DTLS connection. Once the DTLS connection has been established, the decision point in the code described above just starts sending the packets via the DTLS connection instead of the SSL connection. Control packets, on the other hand, always go over the SSL connection.
The key point is if the connection is considered healthy. If DTLS, an unreliable protocol, is in use and the DTLS connection has gone bad for whatever reason, the client does not know this until Dead Peer Detection (DPD) occurs. Therefore, data will be lost over the DTLS connection during that short period of time because the connection is still considered healthy. Once DPD occurs, data will immediately be set via the SSL connection and a DTLS reconnect will happen.
The ASA will send data over the last connection it received data on. Therefore, if the client has determined that the DTLS connection is not healthy, and starts sending data over the SSL connection, the ASA will reply on the SSL connection. The ASA will resume use of the DTLS connection when data is received on the DTLS connection.'
